- Joined
- Mar 23, 2016
- Messages
- 2,393
- Reaction score
- 2,153
- Location
- Bavaria / Germany
- Website
- h-elsner.mooo.com
The build-in read protection of the STM32 processor family is not so easy to hack. I read nowhere that someone did it.As a next step you can reverse the flashing process and inject a small code, to read bootloader. Possible this or not IDK. But to read back the flash area should be possible. For sure there is a checking process after block writing.
EEPROM is a part of flash...
You need a licence file. FC checks it. Message57 uploads the licence. I don't want to make this public because I want not be responsible if someone makes thumb things...Take e look how the switches are handled via serial. As example NFZ. There should be more switches in FC. Commands are not encrypted (I guess).
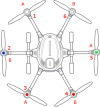
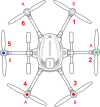
"So, what is right? Can someone confirm, that Q500log2kml motor_status interpretation is right, with other words, when it says this motor is affected, is this motor affected then?"View attachment 31572
Again, this was my understanding up to now.
So, what is right? Can someone confirm, that Q500log2kml motor_status interpretation is right, with other words, when it says this motor is affected, is this motor affected then?
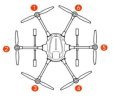
And what is the use case for that?A possible way to duscover foreign CSV's is to make anogher application, which will act as drone and to connect the GUI to the simulated feed via UART.
This will give a possobility to play the file, to stop, to revert (as media player)
We use essential cookies to make this site work, and optional cookies to enhance your experience.


